What is a Cache? Understanding Its Role and Benefits of Clearing It
In computers the essential caching method involves putting commonly retrieved data into quick-access storage locations. As an essential method, caching operates throughout different technological systems that cover web browsers and operating systems and also includes CPUs and other hardware components. The key reason to implement caching is to enhance performance by allowing faster access to slower storage systems.
What is a Cache?
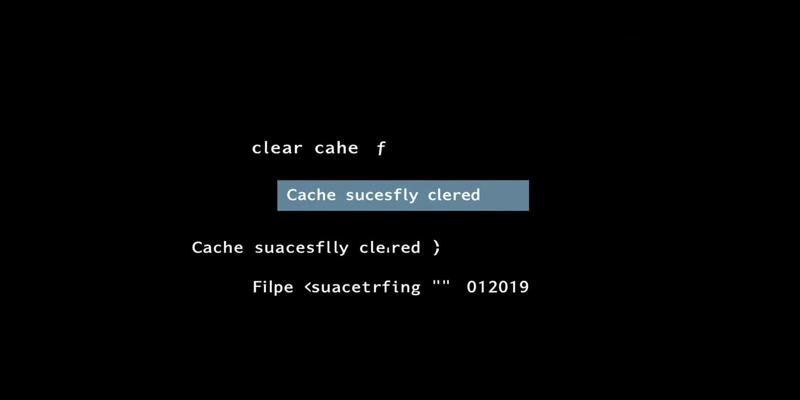
Data storage located in a temporary area functions as a cache for efficient retrieval access. This storage facility serves as a speed accelerator between main memory and slower storage devices including hard drives and internet access. Enhanced system performance results from keeping data that is commonly used in these faster storage areas.
Types of Caches
- Web browsers implement browser caching as a feature to store website elements including images and both scripts and stylesheets. Web pages will load more quickly upon returning to a website because of this data storage capability.
- System Cache operates as a feature in operating systems which enhances file access speed through RAM storage of frequently accessed files or their parts.
- Data and instructions can temporarily stay inside CPU-built caches until processors complete their processing operations. This significantly speeds up computation.
- Storage devices that consist of hard drives and solid-state drives use caching to speed up disk read and write procedures.
Why Does Clearing the Cache Fix Things?
- Clearing the cache helps solve various problems that develop from invalid or damaged cached data. The following list explains how clearing the cache provides benefits:
- The data stored in a cache may become old when the source it came from undergoes modifications. Clearing the cache makes the system obtain current versions of all data from its sources.
- The storage of cached data might become corrupted which results in system display errors alongside incorrect information. The clearing process deletes corrupted data thus the system obtains fresh accurate information.
- Privacy risks emerge because cached data contains private information which includes data related to user credentials along with browsing history. The clearance of cached data serves as a privacy protection mechanism by deleting the stored data.
- The expanding cache file size leads to storage space saturation which causes system performance problems. The procedure of clearing cache enables your system to utilize additional storage space thus boosting its operational performance.
- The stored data in cache may experience compatibility problems when compared to latest software and website versions so this leads to system incompatibility issues. Clearing the cache solves these problems through its function of only using data that is compatible with the system.
How to Clear Cache

The process of clearing cache depends on the type of cache system alongside the platform.
Clearing Browser Cache
- Users of Google Chrome must access Settings then Privacy and security followed by clearing the browsing data.
- Users of Mozilla Firefox should select Options then Privacy & Security before moving to Cookies and Site Data then Clear Data.
- Safari users can reach Cache management through Preferences and Privacy and then use Manage Website Data to pick Remove All.
Clearing System Cache
- The Disk Cleanup tool combined with third-party software enable users to erase system files and temporary data under the Windows operating system.
- Open About This Mac on macOS then check the Storage tab to control storage utilization and execute system file cleanup.
Clearing CPU Cache
The CPU manages CPU cache automatically which requires no intervention from users for clearing operations.
Benefits of Caching
The option to clear caches becomes necessary from time to time but caching provides various useful features.
- Data caching enables faster retrieval of popular data which results in increased system performance together with better user experience.
- Web content caching enables local storage of the most frequently used resources, thus minimizing server requests, decreasing network data movement, and boosting network speed.
- Systems that enjoy quick data retrieval functions with efficiency that results in power savings.
Cache and Its Impact on Software Updates
When application updates occur, the stored cache data could produce installation issues or software compatibility problems. An update process for systems and applications requires fresh data, while conflicts may happen if cached data keeps outdated files. The mobile app crashes or malfunctions due to its incorrect reference of outdated cached files instead of using updated data.
Clearing the cache post-update guarantees that the software uses the proper and most recent data allocation. Operating systems and their frequently updated applications require specific attention to cache cleaning because outdated data stored in the cache can heavily affect their stability and overall performance.
Security Risks Associated with Cached Data
The storage of cached information in a system creates both speed enhancements and security threats. Sensitive materials, including login details and browsing histories or user preferences might become targets for hackers because they wait in the cache storage. Any unauthorized party can obtain device data stored in the cache when the device is shared or compromised.
The security risk from exposed personal data can be eliminated through routine cache cleaning because it deletes stored information traces. Certain websites maintain session data within the cache while users remain logged in so that the failure to clear the cache enables unauthorized access to their accounts after logout. The clear deletion of browser cache functions as an outstanding security practice for privacy seekers needing to protect their online data.
Balancing Cache Benefits and Drawbacks
Performance enhancement from caching depends on a proper equilibrium involving speed gains versus notable disadvantages. Heavy use of cached information produces outdated data, while regular clearing of the cache slows down system performance because it requires additional data retrieval.
Users should make their cache clearance schedule match their usage requirements since power users need to clean up their browser cache weekly, but casual users may do so each month. The ability to comprehend caching operations in browsers and apps along with operating systems enables users to determine their clearing strategy effectively for a smooth and protected computational process.
Conclusion
System performance improvements can be achieved by caching because it enables quick retrieval of popular data. The storage of frequently accessed data in the cache is prone to becoming outdated or corrupted until users clear the cache to fix related issues. The understanding of caching operations combined with appropriate cache-clearing practices enables users to preserve efficient and secure system operations.
On this page
What is a Cache? Types of Caches Why Does Clearing the Cache Fix Things? How to Clear Cache Clearing Browser Cache Clearing System Cache Clearing CPU Cache Benefits of Caching Cache and Its Impact on Software Updates Security Risks Associated with Cached Data Balancing Cache Benefits and Drawbacks ConclusionRelated Articles

Which Are The Top AI Art Generators to Unleash Your Creativity in 2025

Which Are The 8 Best Database-Powered App Builders for Seamless Development
How to Fix Trello Boards That Load Slowly or Lag Frequently

10 Must-Have Tools for Effective User Acceptance Testing

Which Are The Best Ways to Automate OneDrive for Effortless File Management
Convert DOCX to TXT Files in Batches Online with No Downloads

How to Fix Slack Lag and Speed Up Notifications Effectively

Troubleshooting Cloud Storage Sync Errors: A Step-by-Step Guide

Whitelisting Guide: Allow Safe Websites Blocked by Antivirus

Choosing the Right App Builder for Your Needs

The Best Email Drip Campaign Software: Top Picks for Seamless Automation

 knacksnews
knacksnews